CrediX DeFi Protocol Loses $4.5 Million in Admin Access Attack
A major security breach hit the decentralized finance world on August 4, 2025, when hackers stole $4.5 million from CrediX, a lending protocol built on the Sonic blockchain. The attack highlights ongoing problems with how crypto projects manage access to their systems.
The hackers didn’t break into CrediX through code flaws or smart contract bugs. Instead, they gained control by getting administrative access to the protocol’s multi-signature wallet system. This type of attack has become the biggest threat to crypto projects in 2025.
How the Attack Happened
Security firm SlowMist reported that the attackers planned their move carefully. Six days before the theft, someone added the attacker as both an Admin and Bridge controller to CrediX’s multi-signature wallet through the protocol’s access control system.
With these special privileges, the hackers could mint fake collateral tokens directly through CrediX’s lending pool. They used these worthless tokens to borrow real cryptocurrency from the protocol, essentially draining the available funds.
Source: @CrediX_fi
Blockchain security company PeckShield identified the compromised wallet ending in “EC662e” that carried out the exploit. This wallet had multiple high-level roles including pool admin, bridge controller, asset listing admin, emergency admin, and risk admin powers.
The stolen money was quickly moved from the Sonic network to Ethereum, where it sits in three separate wallets. Security firm CertiK confirmed the attackers haven’t tried to cash out through exchanges yet.
CrediX Background and Response
CrediX launched just last month as a real-world asset lending protocol. The Belgium-based company has raised $73.7 million in funding and focuses on connecting investors with small lenders in emerging markets.
The protocol marketed itself as an aggregator that lets users access multiple DeFi platforms like Compound and Aave in one place. CrediX claimed users could earn over 10,000% annual interest rates by lending through their platform – a promise that echoes failed crypto lenders from previous market cycles.
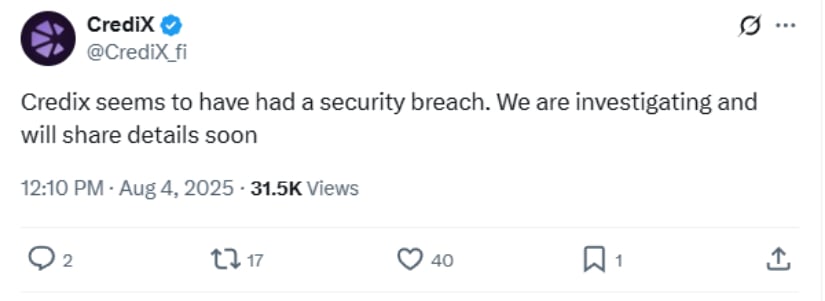
After discovering the breach, CrediX shut down its website to prevent new deposits. The company posted on social media that it was investigating and promised to recover all stolen funds within 24 to 48 hours.
Possible Recovery Agreement Reached
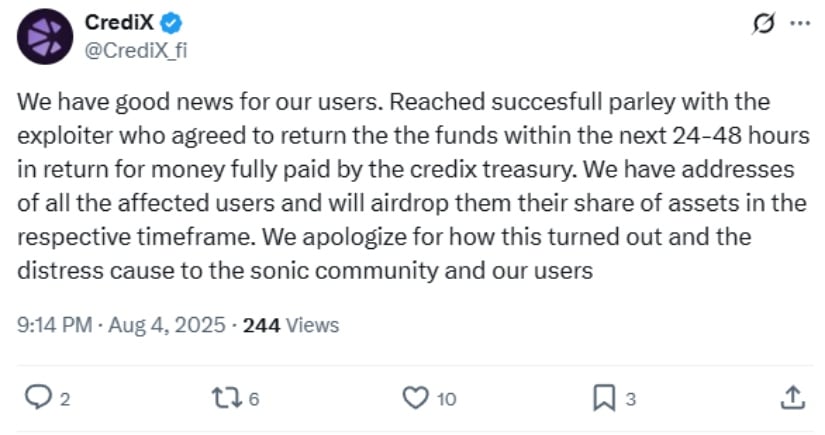
In a positive development, CrediX announced they reached an agreement with the attacker to return the stolen funds. The exploiter agreed to give back the $4.5 million within 24-48 hours in exchange for payment from CrediX’s treasury. The company said they have identified all affected users and will distribute recovered assets through an airdrop system. CrediX apologized to both the Sonic community and their users for the incident.
Source: CrediX_fi
Part of a Bigger Problem
The CrediX hack fits into a troubling pattern for crypto security in 2025. According to security firm Hacken’s report, hackers have stolen $2 billion from crypto projects in just the first quarter of this year.
Most of these attacks targeted multi-signature wallets through social engineering, fake interfaces, or poor management of signing permissions. The biggest single theft was $1.46 billion from the Bybit exchange, where attackers tricked authorized signers with a fake interface.
Access control failures account for over 80% of all crypto losses in 2025. Traditional smart contract bugs that dominated previous years now make up less than 2% of total stolen funds.
Why Multi-Sig Wallets Keep Getting Hacked
Multi-signature wallets require multiple people to approve transactions, which should make them more secure than regular wallets. But many projects don’t set them up properly or give too much power to individual signers.
In CrediX’s case, adding a single new signer with both admin and bridge roles created a single point of failure. The attacker only needed to compromise one set of credentials to gain complete control over the protocol’s funds.
Security experts say many DeFi projects treat comprehensive security as something to improve over time, rather than a requirement before handling millions in user money. This approach leaves users vulnerable while protocols focus on attracting investments and launching quickly.
Hacken now recommends that crypto projects move away from one-time security audits. Instead, they should use real-time monitoring systems powered by artificial intelligence to watch multi-signature wallet activity and flag suspicious behavior immediately.
What This Means Going Forward
The CrediX attack shows that governance and access control remain the weakest links in DeFi security. As more projects rush to launch and attract funding, proper security practices often get pushed aside.
Many DeFi protocols keep centralized admin controls during their early stages, which creates opportunities for attackers who can gain access to these powerful accounts. Projects need better oversight of who gets administrative access and stronger community approval processes for important changes.
The crypto industry has seen this cycle before – major hacks followed by promises to improve security, only to see similar attacks happen again. Until projects prioritize robust security from day one, users will continue losing money to preventable attacks like the one that hit CrediX.