North Korean Hackers Distributing Trojanized DeFi Wallet Apps to Steal Victims’ Crypto
The North Korean state-backed hacking crew, otherwise known as the Lazarus Group, has been attributed to yet another financially motivated campaign that leverages a trojanized decentralized finance (DeFi) wallet app to distribute a fully-featured backdoor onto compromised Windows systems.
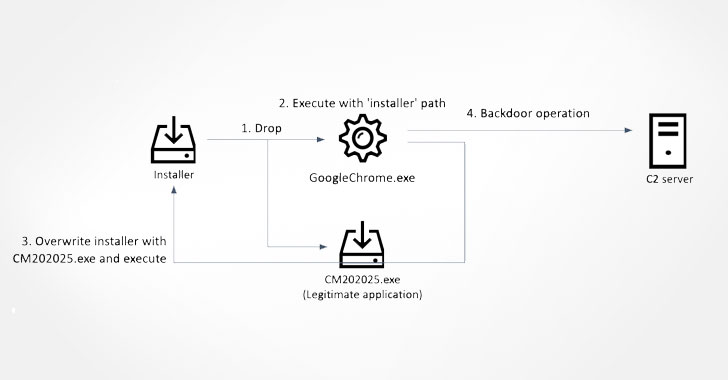
The app, which is equipped with functionalities to save and manage a cryptocurrency wallet, is also designed to trigger the launch of the implant that can take control of the infected host. Russian cybersecurity firm Kaspersky said it first encountered the rogue application in mid-December 2021.
The infection scheme initiated by the app also results in the deployment of the installer for a legitimate application, which gets overwritten with a trojanized version in an effort to cover its tracks. That said, the initial access avenue is unclear, although it’s suspected to be a case of social engineering.
The spawned malware, which masquerades as Google’s Chrome web browser, subsequently launches a wallet app built for the DeFiChain, while also establishing connections to a remote attacker-controlled domain and awaiting further instructions from the server.
Based on the response received from the command-and-control (C2) server, the trojan proceeds to execute a wide range of commands, granting it the ability to collect system information, enumerate and terminate processes, delete files, launch new processes, and save arbitrary files on the machine.
The C2 infrastructure used in this campaign exclusively consisted of previously compromised web servers located in South Korea, prompting the cybersecurity company to work with the country’s computer emergency response team (KrCERT) to dismantle the servers.
The findings come more than two months after Kaspersky disclosed details of a similar “SnatchCrypto” campaign mounted by the Lazarus sub-group tracked as BlueNoroff to drain digital funds from victims’ MetaMask wallets.
“For the Lazarus threat actor, financial gain is one of the prime motivations, with a particular emphasis on the cryptocurrency business. As the price of cryptocurrency surges, and the popularity of non-fungible token (NFT) and decentralized finance (DeFi) businesses continues to swell, the Lazarus group’s targeting of the financial industry keeps evolving,” Kaspersky GReAT researchers pointed out.






