Watch Out! North Korean Crypto Hackers Are Getting Smarter
North Korean crypto hackers continue to send tremors through the cyberspace as they get smarter and more relentless. According to recent reports, their nefarious activities are rising, morphing, and evolving with alarming speed and sophistication.
The secrecy-shrouded regime of North Korea is leveraging its expanding army of information technology (IT) experts. It aims to fund its military ambitions, sidestepping international sanctions with a chilling audacity that has governments worldwide on high alert.
The Rise of North Korean Crypto Hackers
The United States and South Korean officials recently expressed serious concerns over North Korea’s plans to dispatch more IT workers overseas. It was seen as a strategy to intensify crypto hacking activities and bolster military funding.
According to Deputy Special Representative for the Democratic People’s Republic of Korea, Jung Pak, North Korea is preparing to expand its clandestine digital workforce as it anticipates easing the stringent COVID-19 lockdown.
“This is a growth industry, because as we see the DPRK potentially opening up borders, they could be dispatching additional laborers to all parts of the world to generate revenue. We think it’s actively getting worse,” said Pak.
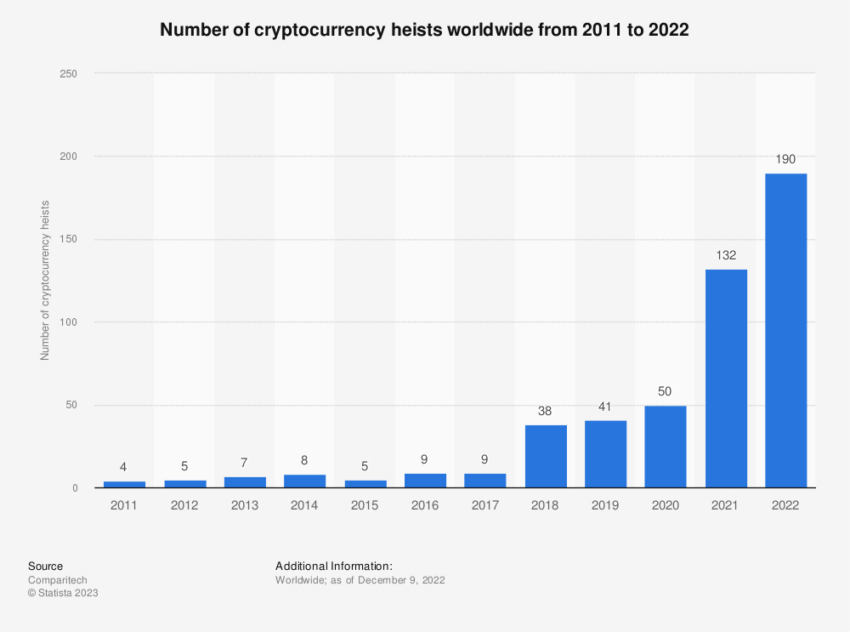
For North Korea, faced with Western-imposed sanctions and the crippling effects of the COVID-19 pandemic, the crypto market is a new frontier teeming with opportunities. The allure of crypto and the rise of information technology have prompted the nation to concentrate increasingly on making money out of the cyberspace.
An alarming United Nations Panel of Experts report estimated North Korean hackers to have stolen between $630 million to over $1 billion worth of cryptocurrency in 2022 alone. The report highlighted that the regime’s profit-driven hacking operations are “low-risk, high-reward and difficult to detect, and their increasing sophistication can frustrate attribution. ”
Operational Tactics: Inside the Cyber Espionage
North Korean crypto hackers excel in identity deception. They routinely disguise their locations, nationalities, and identities. Moreover, they operate behind false personas, falsified documents, and proxy accounts to secure jobs globally.
Their targets are rich countries, with specific sectors like business, health and fitness, social networking, sports, entertainment, and lifestyle in their crosshairs.
A key player in this unscrupulous endeavor is Kimsuky. Indeed, this North Korea-based cyber espionage group is known to have stolen weapon and satellite development technologies.
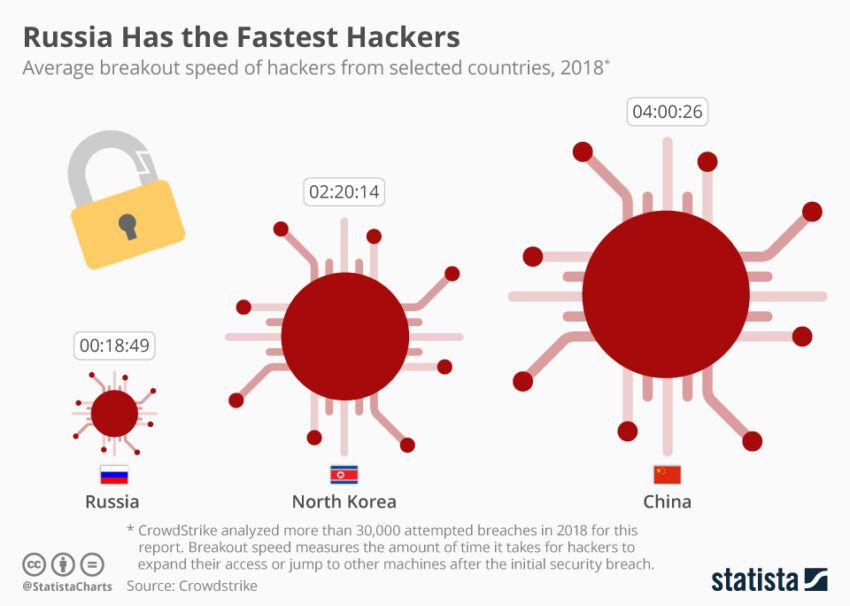
The notorious organization employs scams, theft, cryptojacking, and sextortion tactics to fund its operations. Moreover, it cleverly uses cryptocurrency to obscure its illicit transactions.
Last year, a North Korean operation masquerading as a job recruiter lured an unsuspecting engineer from the blockchain gaming company Sky Mavis. This malicious Trojan Horse led to an over $600 million theft — mainly from players of the digital pets game Axie Infinity.
This crypto heist, the country’s largest in five years, funneled considerable resources into North Korea’s ballistic missile program.
Global Impact of North Korea’s Digital Crimes
The rampant cyber criminality by North Korea’s digital brigands has caused great consternation in international circles.
Anne Neuberger, US President Joe Biden’s deputy national security adviser for cyber and emerging technology, noted the significant surge in large-scale cyber heists targeting crypto infrastructure. This trend has forced the US to ramp up its efforts to counter this threat.
“The real surge in the last year has been against central crypto infrastructure around the world that hold large sums, like Sky Mavis, leading to more large-scale heists. That has driven us to intensely focus on countering this activity,” said Neuberger.
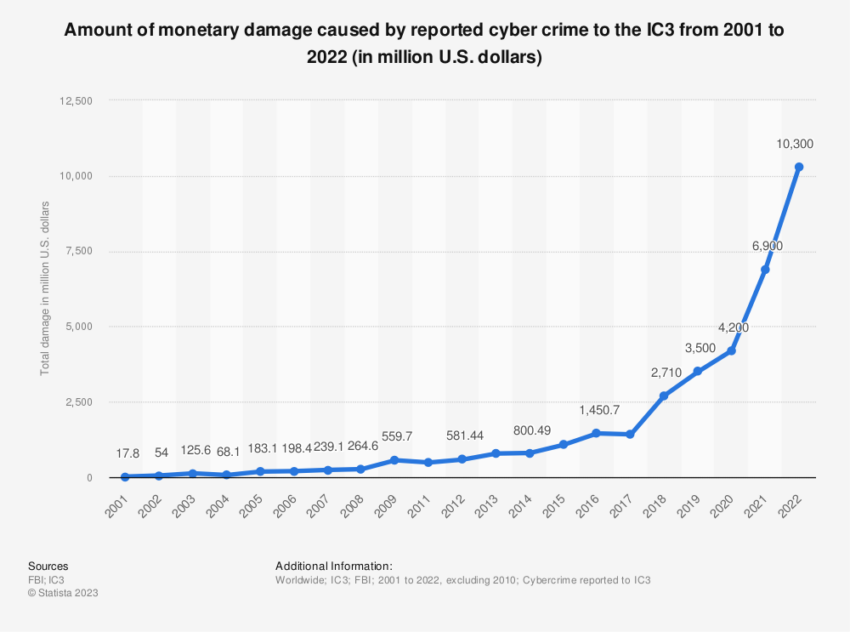
Interestingly, North Korea’s wave of successful missile launches in recent years coincides with the uptick in crypto heists. A definitive correlation cannot be established due to the opaque nature of North Korea’s financial resources. Still, it is evident that crypto hackers play a significant role in funding its missile program.
North Korea has also constructed a global shadow workforce of IT workers, many operating from allies like Russia and China. Indeed, these individuals earn substantial amounts annually. They are often tied to the regime’s cybercrime operations, further deepening international investigators’ challenges.
Strengthening International Response
Given these circumstances, the ongoing evolution of North Korea’s crypto-hacking abilities is a cause for global concern. Certainly, their advanced, sophisticated tactics highlight the critical need for vigilance, improved cyber defenses, and strengthened international cooperation.
As the North Korean crypto hackers grow smarter, the world must stay ahead. Consequently, continuously fortifying its defenses in this digital cat-and-mouse high-stakes game.
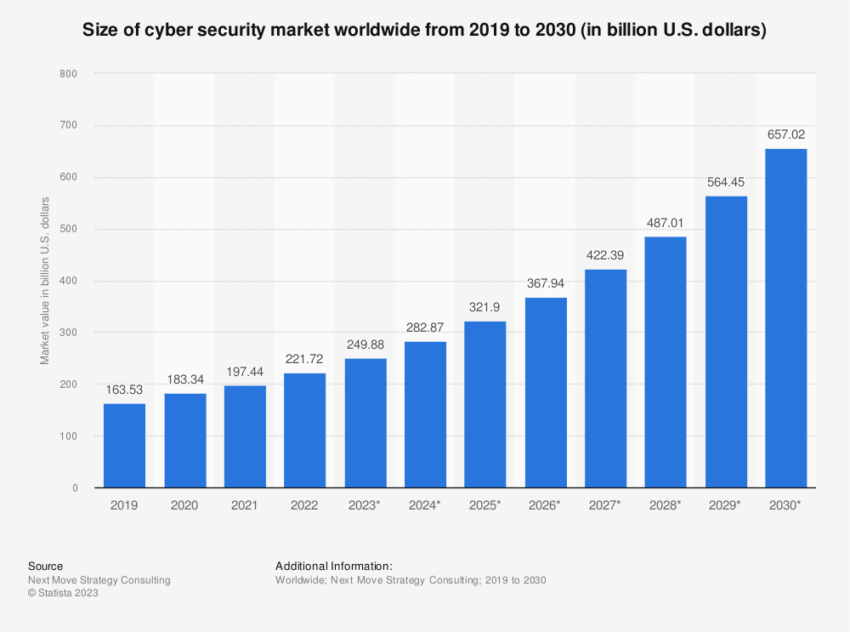
The troubling tale of North Korea’s expanding digital crimes underscores the complex challenge that governments, financial institutions, and tech companies face today. For this reason, a swift, robust, coordinated international response is crucial to ending these ever-escalating crypto hacks.
Disclaimer
Following the Trust Project guidelines, this feature article presents opinions and perspectives from industry experts or individuals. BeInCrypto is dedicated to transparent reporting, but the views expressed in this article do not necessarily reflect those of BeInCrypto or its staff. Readers should verify information independently and consult with a professional before making decisions based on this content.


